
The pandemic has enclosed us within our residents. We all work remotely, and video conferencing has become an essential part of our lives.
Enhance Safety for Online Meetings
Summarize with
Table of contents
The hackers invade webinars and get the password. Imagine your valuable webinar equipment, information, and the company’s secret being out in public. It can also disrupt the E-learning process. In the list of countries with the most hackers, China is at the top. These are more harmful than it seems for online meeting security. Recently FBI and other cybersecurity agencies have warned the users regarding this.
Cyber hacking has cost the US $57 billion to $109 billion. Therefore, the security of video conferencing shall be the utmost priority of the organizations. I am going to elaborate on simple steps. By using these steps, you will be able to secure your online meetings.
1. Create a meeting password
Your unique link and password are your webinar’s first line of defense. Have you heard of a Brute Force Attack? It is to hack your account by guessing the link and password. Every 1 in 5 attempts is successful.
You should not use a public link and password among the employees. The attendants of meetings must be provided with a link and password to curtail any potential chance of intrusion.
If you are using MyOwnConference, then it’s more convenient for you. They provide a two-fold authentication option for tighter security.
Select the profile option at the left corner of the screen.

Disable the two-fold authentication option.
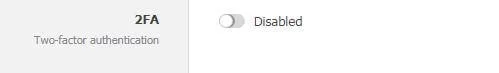
This feature is also available in other upgraded applications. So there is no need to worry about that. Though, you should be worried about the password you are setting. Always set a complicated password for authentication.
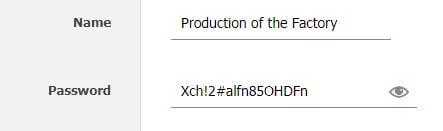
These passwords must be long and complicated enough to be unable to memorize. Use a blended combination of letters, special characters, and numbers.
Trust me, using ‘1234’ of ‘name of organization’ is relatively outdated. Select a diverging name for your meeting.
2. Lock everyone
When you plan a meeting, you should have a list of all the employees attending the meeting. Set the maximum time limit for the employees to join.
After that time, you should lock your video conference. This feature will provide additional benefits in securing the conference. It will create more difficulty for the hacker to intrude and acquire valuable information.
You can make a list of the attendee and their present status at the conference.
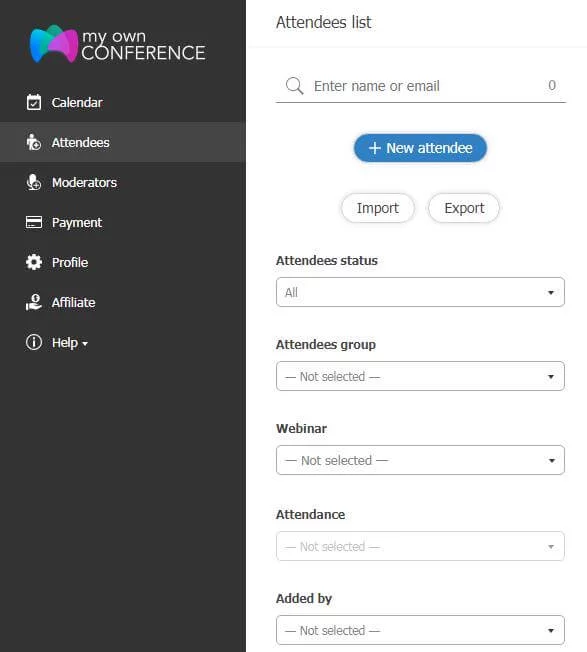
The app provides an available option for employees. Also, you can add them before the start of the meeting. You should add only authentic people to the meeting. What I found attractive in this is the added-by option.
I knew a single person, especially a boss or a manager, could not host the conference; there shall be more than one person or advanced webinar equipment. This feature will provide you with information about whoever has added a new person.
3. Video link sharing rules
What you can do to exempt the proportionality of any harmful effect is to take precautionary steps. While sharing the link to the video conference, you should be careful.
I do not suggest you use public platforms for sharing video links. I mean, do not post on Facebook or Instagram or the office groups at WhatsApp.
This will deliver the details to an unnecessary person also. What you can do is to write inviting emails to every individual. I knew it is quite a work, but prevention is better than cure.
After this, you have to provide your employees with a draft of rules that everyone must follow to ensure the video conference’s security. It is necessary to make it creative and secure, as 56% of employees consider it worthless. This can include general postulates;
- You are not permitted to share link and password with anyone without prior permission.
- You are not permitted to post any video clip from the conference.
- Posting the link of the conference on any social platform will be considered cybercrime and privacy invasion.
In MyOwnConference, if you only want the original invitees to be able to join the meeting, click the button so that the attendees can only join with their personal invitation link.
4. Create a waiting room
A waiting room for the conference attendee is essential to be prepared. This room will serve similar functions as a waiting room does in an office.
Employees will have to gather and wait in this virtual room till all the employees are present.
This will reduce the hassle of waiting for all the employees to be adequately present at the same time.

This will also support you in controlling the entrance and exit of the attendee. You are in charge of your online meeting.
It would be best to decide who will be in the meeting and who will not be. MyOwnConference provides you with an opportunity of creating a moderator list.
This is similar to the waiting room. In this, you can add an attendee and wait till all of them are active.
5. Unknown phone numbers
I hope by now, you can conduct a secure video conference. Yes, your conference is indeed safe from any external threat. But what if the threat is from inside? Not intentionally, but unintentionally, employees can get involved in victimizing the conference.
Therefore, you must ensure that no one is dialing an unknown number during the conference.
It is your responsibility to keep an eye on every aspect of the meeting. Immediately ask your attendee if they dial any unknown number. Inquire them about the details and reasons for dialing the number.
In case of any inappropriate answer, you can expel them from the conference. To join the meeting from a cellphone is an additional benefit. But I’ll suggest you use the platforms that support desktops only for screen sharing.
6. File sharing limit
During the video conference, you should restrict the file sharing option on the message column. This would enable any outsiders to invade the private document. Or to send any disguised material to any of the attendees.
The option of limiting file sharing differed in different applications. You can either enable it entirely from the account or enable it for a specific group of people. From my perspective, limiting the type of file to share is the best option to include in the e-learning process.
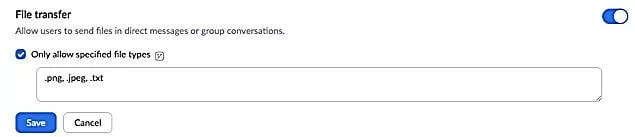
It is more convenient ad easier to conduct. First, you have to click on the IM setting in the account management option.
Select the file transfer option and write the format of the file that you can use.
7. No recording
As I have told you above regarding the Zoom bombing and the unintentional behavior of the employee. This one is also related to both of them.
The screen sharing feature facilitates all the attendees to share and control the screen. They will be able to record the whole video conferencing.
Imagine that there is an intruder in your video conferencing and recording all the information without any interruption despite all your efforts. Will you be able to trace him? I guess no, because of the silence.
Therefore, this step is obligatory. The limitation of screen sharing limits the recording option. The employees can also do this to create a cheerful environment alter. But it is still harmful to the organization.
This is why; you should strictly disperse the policy of no screen recording and limit screen sharing.
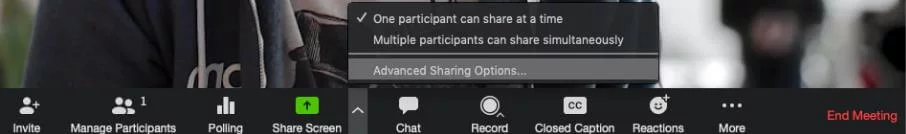
Don’t get worried about the deliverance of information. You can add a selective attendee to the list to share the screen after the conference starts.
But the initial sharing of the screen is not recommended.
8. Audio only
You can also try the audio-only option for the meeting. In this, you will reduce any possible chances of screen recording or leaking any valuable information.
You can request your employees to shut off their webcam and participate from audio-only. It also takes lesser bandwidth on the internet, increasing the quality of the conference.
I knew it seems a little weird, a video conference without video, but for the conference’s security. Don’t get worried about the quality of the audio voice. You can increase it by using different options.
I’ll provide you with the details regarding Zoom. Well, it is commonly present on every platform.
You can either put your meeting on speakers. Make sure you don’t disturb other people.
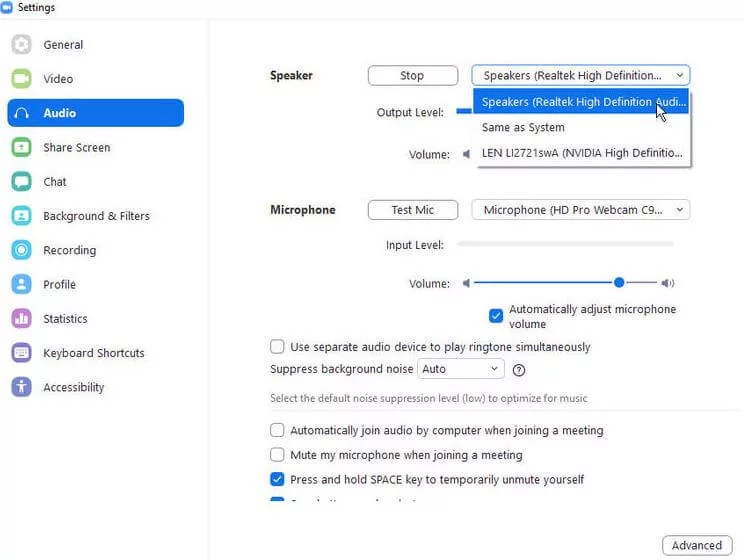
If your area is uncomfortable from this. You can use the advanced microphone setting.
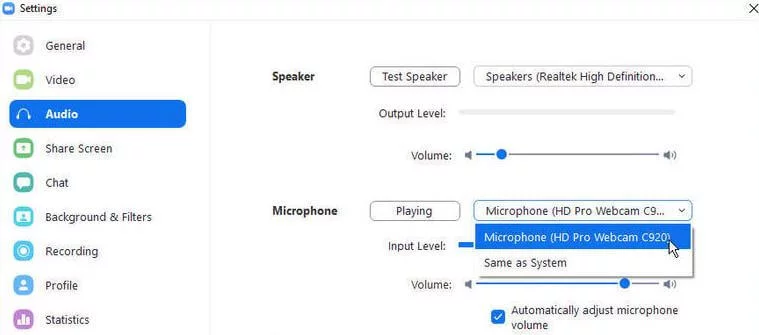
Wait, I have more to elaborate on. You can also suppress the background noise if it bothers you or creates hurdles in understanding the audio.
9. Use a license
The video conferencing tools and applications in the present era are necessary for the organization, not a luxury.
The organization shall buy its licensed tool rather than utilize the free-of-cost features. The licensed tool will provide you with additional safety features for securing your video conference.
The MyOwnConference will cost you only $29 per month. It also provides the long-life free trial version.
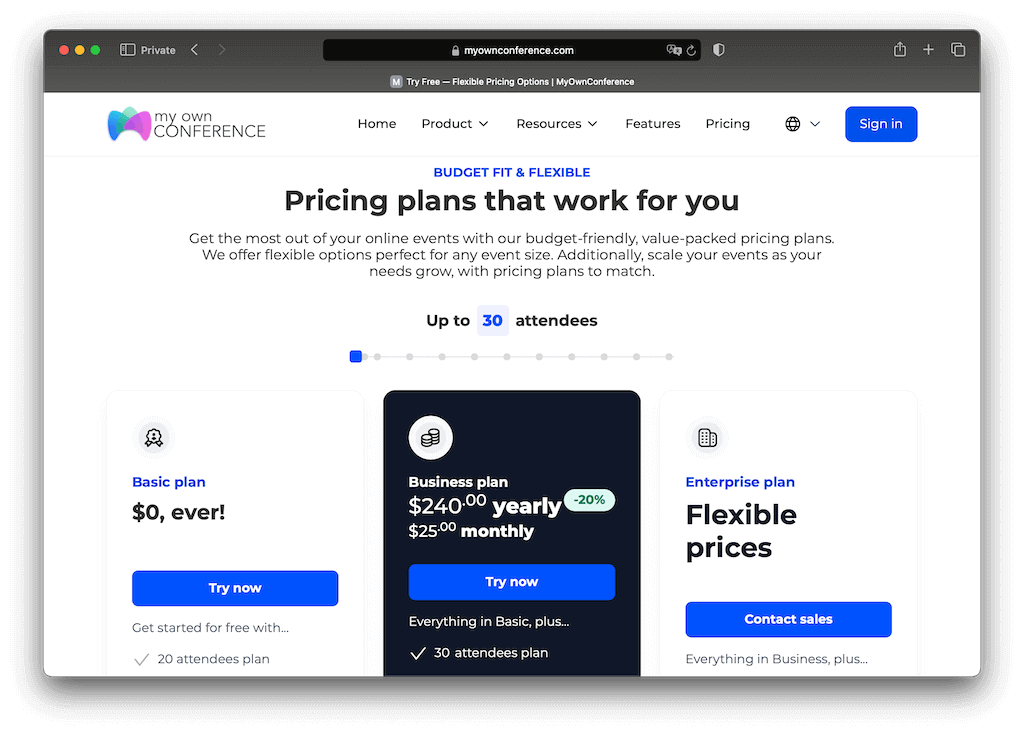
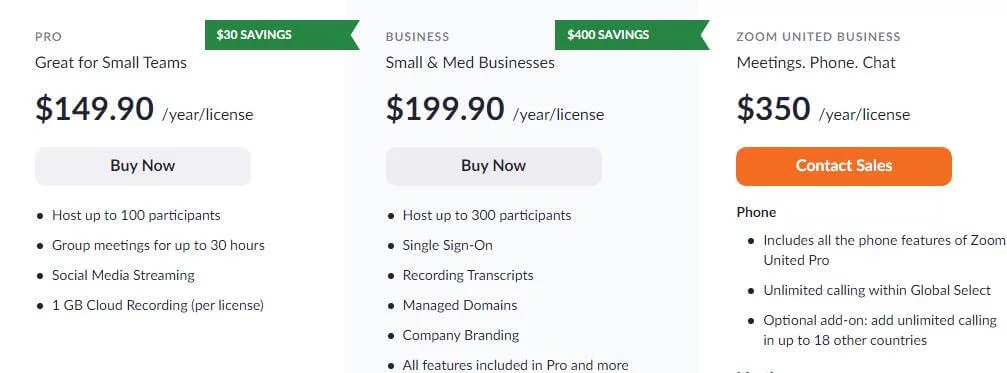
The free-of-cost features are public and may expose your conference to more threats. You can buy the large meeting facility of Zoom, costing only $500/month.
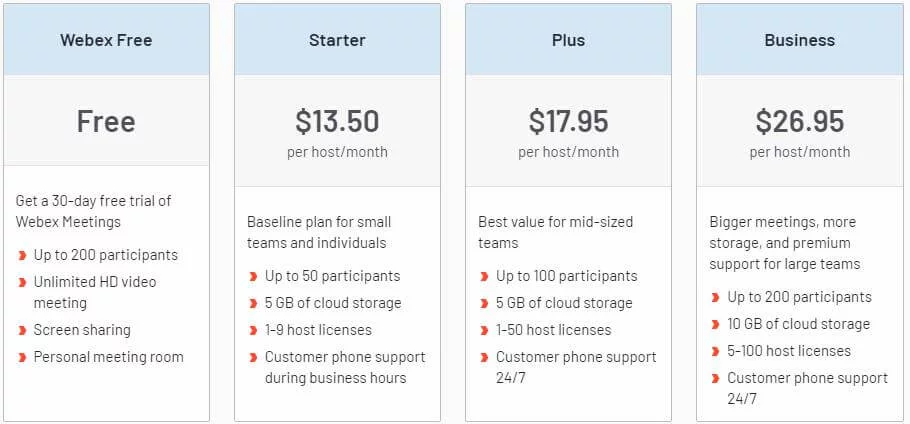
The Cisco Webex starts from $13.50/month.
10. Set up alerts
I knew this all sounded like a minor hassle for the executive to handle in a single video conference. I have a more convenient option for you.
You can use the alert options in the applications. Yes, the technology is evolving for the benefit; there is a solution for your every difficulty. You can customize alert options. This will alert you whenever an undesired activity occurred. Now let me explain the undesired activity.
Well, this is dependent upon your company’s security guidelines. Generally, it refers to forwarding invite emails to any unauthorized person, recording video or taking screenshots.
I’ll mention here the Cisco Webex features, it is available in every video-conferencing application to increase online meeting security.
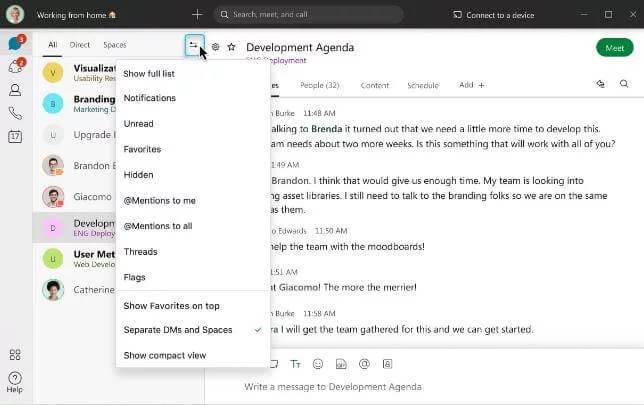
Zoom also provides these services. The services provided by Zoom are more convenient and advanced.
Final words
Hosts can practice several safety precautions during the meeting to eliminate the chances of intrusion. I am not saying that these will entirely out throw hackers, but they will be effective to some extent.
The IT firms’ advanced teams draft these precautions, and it is not that much easier to invade. But there is still a risk of hackers.
Please let me know if you find any other precautions that seem more effective than mine, and I will add them to my next article about security.
FAQ
You should always set a meeting password and send personal invitation links instead of posting the link publicly. You also can lock the meeting once all expected participants have joined and use the waiting room feature to control who enters.
You limit file sharing by disabling it for everyone except trusted participants or by restricting the allowed file types in chat. This helps stop external or malicious files from being shared inside your meeting.
Recording risks leaking sensitive information especially if an intruder is present. To avoid that risk you enforce a no-recording policy and you can run the meeting in audio-only mode so that video is turned off and the chance of misuse is lower.
It is safer to use a licensed version because paid tools typically come with stronger security features. Free plans often miss advanced safeguards which might leave your meeting more exposed to attacks.
Alerts notify you when someone does something like forwarding invites, recording, or taking screenshots without permission. You should enable them before the meeting so you are aware of any unwanted actions as soon as they happen.

Melissa Calvert is a devoted Lifestyle Counselor at Crowd Writer and Dissertation Assistance. The organization from where you can avail of the essay writing service the UK. She is a dedicated and passionate lady. She has served on different platforms to increase the lifestyle of her readers. She is willing to pen down every issue creating an obstacle in the reader’s life.











